Just kidding.
We’re still here.
I remember as a 10 year old playing around with how computers and the internet worked on my Dad’s computer.
It quickly became clear defacing websites, especially at that time, was not hard. Even for a 10 year old.
Similarly, with the amount of insecure technologies around today, namely Wordpress plugins, it’s not that much harder today.
Defacement is a simple attack. It’s often easily reversible and does not (usually) compromise sensitive data.

Though it does make for a nice news story.
The average internet user who finds their banks website now shows a picture of Donald Trump being punched in the face with Persian they cannot understand will panic.
What’s happened to my life savings? Are my details safe? Does my computer have a virus?
Despite the simplicity, many analysts would argue the attackers have achieved their objectives because of the media coverage they’ve garnered.
A lot of website defacements leave the signature of the attacker.
Whether it’s from a group supporting Iran or a lone individual, perpetrators like leaving a message to get credit for their work.
It’s like a graffiti tag or signature. Dave woz ‘ere.
In the world of website defacements, a signature typically starts with “Hacked by”.
This makes it easy to identify “hacked” sites.
A simple search for “Hacked by” in the title of websites returns 1000’s of results on Shodan.
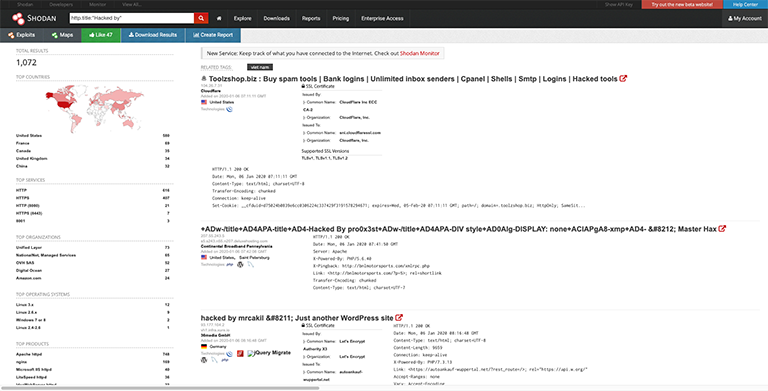
http.title:"Hacked by"
Search for yourself (required a Shodan account).
Finding hacked sites is a fun waste of time between meetings.
Finding your own assets on the internet is much more… fun.
Your websites.
Your databases.
Your Splunk servers that you thought were inside your private network, but are infact public.
If someone else can find it, defacement might be the least of your worries.
ThreatPipes Modules relevant to this post
- BuiltWith: Query BuiltWith.coms Domain API for information about your targets web technology stack, e-mail addresses and more.
- Censys: Obtain information from Censys.io
- SHODAN: Obtain information from SHODAN about identified IP addresses.
- WhatWeb: WhatWeb recognises web technologies including content management systems (CMS), blogging platforms, statistic/analytics packages, JavaScript libraries, web servers, and embedded devices.
- Web Framework: Identify the usage of popular web frameworks like jQuery, YUI and others.

