Star Wars, Frozen 2, (Don’t F**k With) Cats…
How many of the biggest film releases did you see last month?
My opinion. All were good. Particularly Don’t F**k With Cats.
Most of my family are now OSINT investigators, plugging images into Tineye and extracting the EXIF data to map them on Google Earth.
Inspired, here are a handful of ThreatPipes modules that you might find useful during your next OSINT investigation.
Search
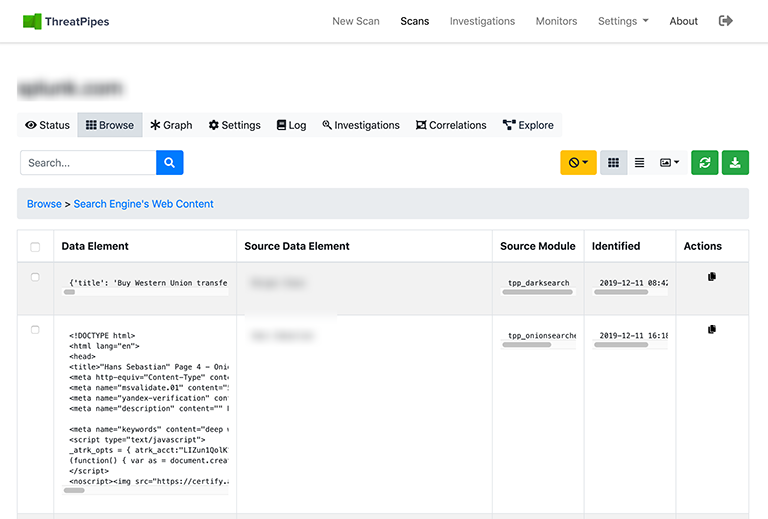
Search engines proved vital in identifying items in Luka’s videos.
Google, Bing, DuckDuckGo, etc. Each search engine has its own strengths. That’s why we search all of them.
If you’re looking to improve your OSINT search skills, check out my post on Google Dorks.
Example ThreatPipes modules you could use to automate web search
- Google: Some light Google scraping to identify sub-domains and links.
- Bing: Some light Bing scraping to identify sub-domains and links.
- DuckDuckGo: Query DuckDuckGos API for descriptive information about your target.
Location
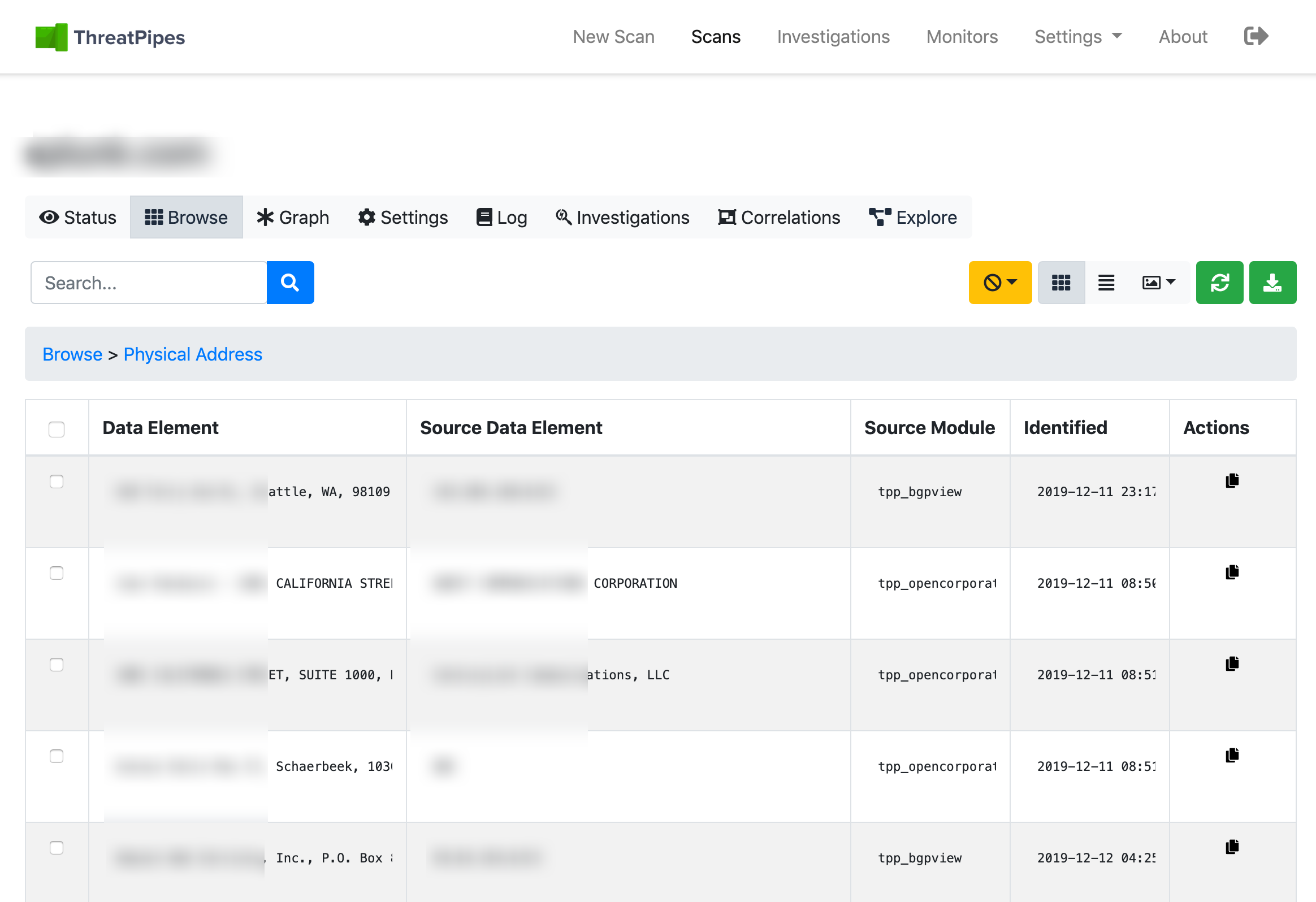
Location was a large part of the teams investigation, chasing Luka from North America to Europe, and back.
Mapping an asset, perhaps by IP address, to a location can be useful.
WiFi networks when tracking a person are a good example.
Example ThreatPipes modules you could use to automate location search
- Google Maps: Identifies potential physical addresses and latitude/longitude coordinates.
- OpenStreetMap: Retrieves latitude/longitude coordinates for physical addresses from OpenStreetMap API.
- WiGLE: Query wigle.net to identify nearby WiFi access points.
Accounts
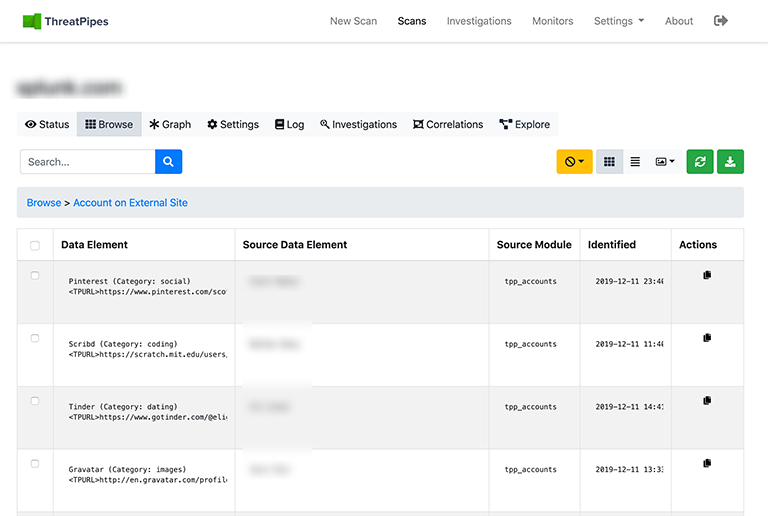
Luka used a number of online persona to spin a variety of stories.
It’s easy to find online accounts created using the same email addresses.
Or accounts with the same user id using the following modules.
Example ThreatPipes modules you could use to automate account identification
- Social Networks: Identify presence on social media networks such as LinkedIn, Twitter and others.
- Social Media Profiles: Identify the social media profiles for human names identified.
- Accounts: Look for possible associated accounts on nearly 200 websites like Ebay, Slashdot, reddit, etc.
Assets
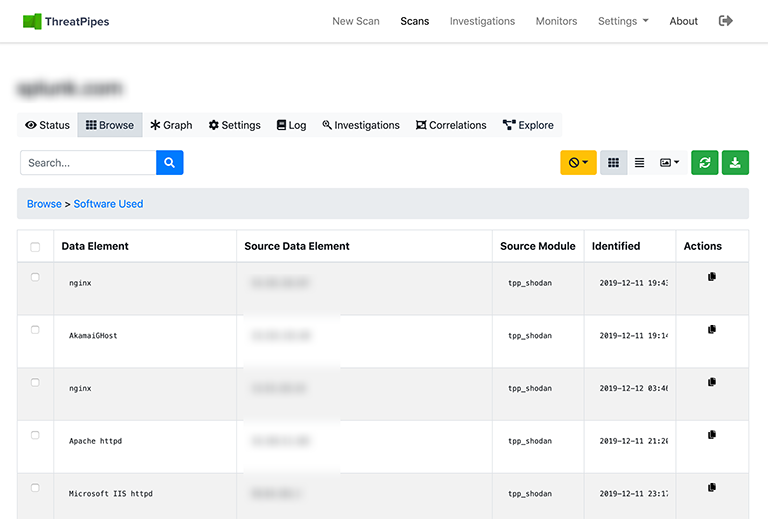
SPOILER ALERT
Luka was caught after a stroke of luck when recognised at an internet cafe.
The arrest was captured by a web cam streaming from the cafe.
Webcams, doorbells, baby monitors… many can be discovered and accessed by tools like Shodan or Censys.
Example ThreatPipes modules you could use to automate asset discovery
- SHODAN: Obtain information from SHODAN about identified IP addresses.
- Censys: Obtain information from Censys.io
- BuiltWith: Query BuiltWith.coms Domain API for information about your targets web technology stack, e-mail addresses and more.

