Did you lock the front door? Yes.
Did you turn off the iron? Let me check.
Did you destroy that old cloud server you provisioned for testing? Errrr.
Did you get around to securing that software properly? Hold my beer.
Two weeks ago we launched the ThreatPipes App for Splunk.
Here’s a demo in case you haven’t seen it yet.
I’ve loved hearing stories about how you’ve been using it, and what you’ve found.
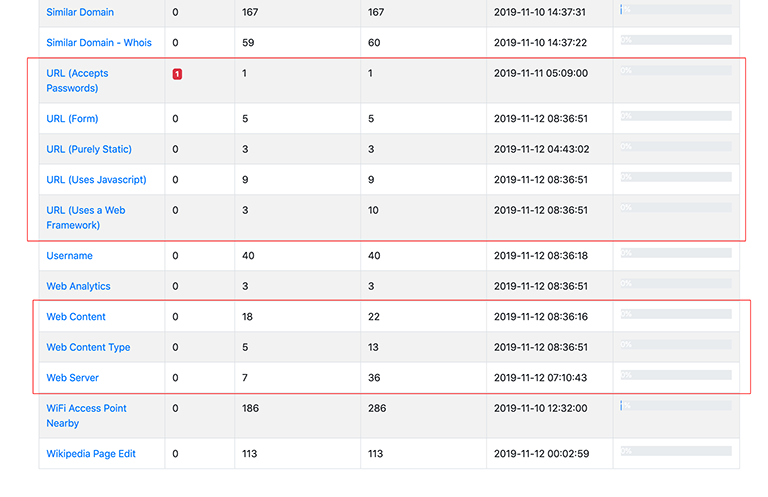
Lot’s of dodgy SSL certificates, badly configured servers, log matches to threat list intel… and Splunk instances.
HTTP/1.1 200 OK
Date: Tue, 12 Nov 2019 19:25:39 GMT
Expires: Thu, 26 Oct 1978 00:00:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, max-age=0
Content-Type: text/html; charset=UTF-8
X-Content-Type-Options: nosniff
Content-Length: 13288
Vary: Cookie
Connection: Keep-Alive
Set-Cookie: cval=REDACTED; Path=/en-US/account/; Secure
X-UA-Compatible: IE=edge
Set-Cookie: splunkweb_uid=REDACTED; Path=/en-US/account; Secure; Max-Age=157680000; Expires=Sun, 10 Nov 2024 19:25:39 GMT
X-Frame-Options: SAMEORIGIN
Server: Splunkd
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=US, ST=CA, L=San Francisco, O=Splunk, CN=SplunkCommonCA/[email protected]
Hello, Splunk Web.
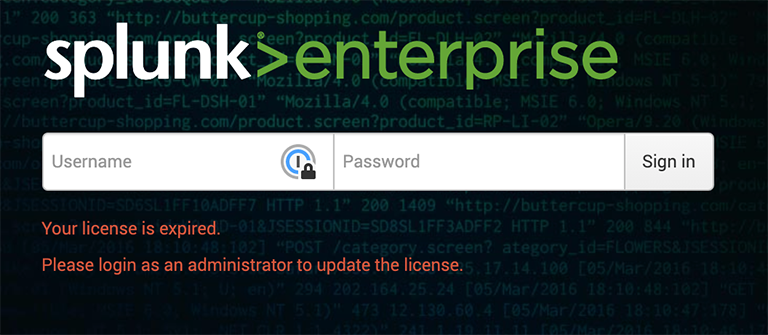
Many very old Splunk webs.
With recent updates it’s not as easy as it once was to break into Splunk. Times have changed since admin:changeme, but humans haven’t.
Mixed with breached account data, companies hosting on their own domains and the use of service accounts, there are lots of weaknesses you need to be aware of when exposing Splunk to the internet like this.
In short; you probably shouldn’t expose Splunk to the internet.
Or any sensitive enterprise software.
Or internet connected front doors.
Do “smart” irons exist yet?
ThreatPipes Modules relevant to this post
- BuiltWith: Query BuiltWith.coms Domain API for information about your targets web technology stack, e-mail addresses and more.
- Censys: Obtain information from Censys.io
- SHODAN: Obtain information from SHODAN about identified IP addresses.
- WhatWeb: WhatWeb recognises web technologies including content management systems (CMS), blogging platforms, statistic/analytics packages, JavaScript libraries, web servers, and embedded devices.
- Web Framework: Identify the usage of popular web frameworks like jQuery, YUI and others.

