When I browse porn sites, I don’t sign up.
In fact, I’ll open up an incognito browser so that Chrome doesn’t log the history locally (I know Google is still tracking me).
Why? I can tell you from experience it’s embarrassing when PornHub shows on the “last viewed” page… as you start a product demo.
Though there seems to be something alluring that attracts some of us to sign up.
Perhaps it’s the ability to save videos for later, when you can’t watch them on the train journey home. Or maybe it’s easier to keep track on the latest videos by your favourite performers by following their accounts. Recommendations welcome.
NOTE: to save some nervous clicks, all the outbound links on this page are safe for work, but you probably shouldn’t click them from a security standpoint anyway.
Of course, they’re not the first. Nor will they be the last site to be breached.
The problem is, this type of breach exposes very sensitive personal data.
Yes, emails, names, potentially passwords (or at least hashes), the usual stuff that makes its way around the internet after a breach.
Though when examining porn site breaches this data might also include “favourite” videos, actors, or search terms.
Pornhub’s top 4 searches by volume were ‘lesbian’, ‘hentai’, ‘milf’ and ‘step mom’ in 2018.
How many of these would you talk about with your boss?
If you said 0, you should stop signing up for porn with your work email.
After my bad experience on the “last viewed” tab in Chrome, having a customer tell you how many of their employees email addresses were uncovered in known porn site breaches makes me wince.
I can imagine the awkward conversations that will follow.
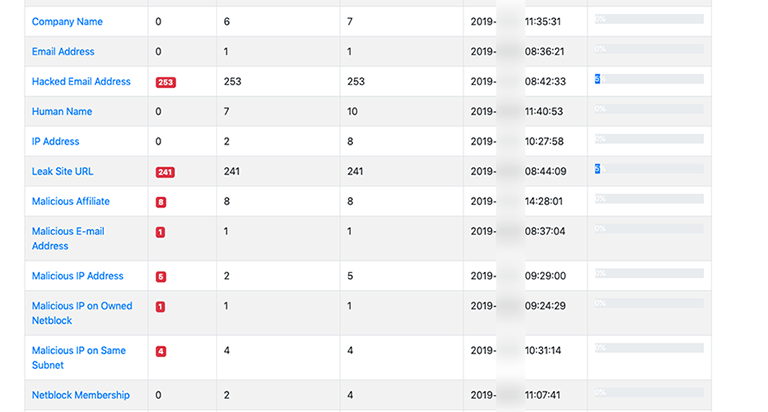
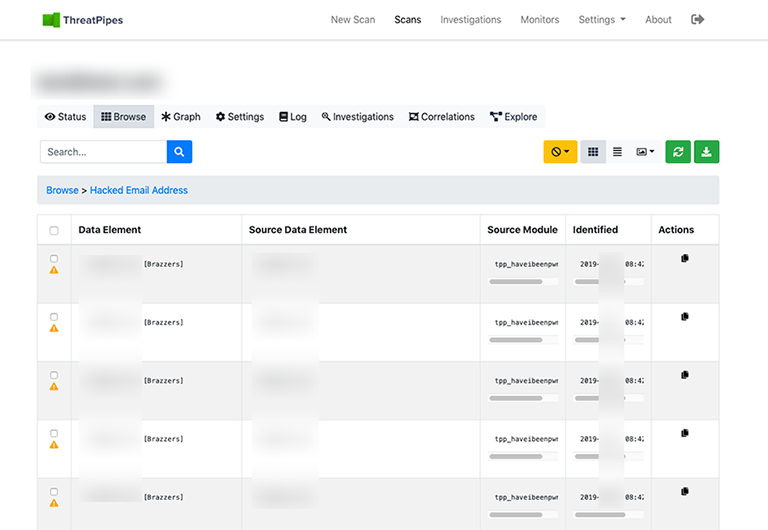
We can sit here an smile, but as Brian points out Sextorion is a real attack vector being used by actors.
Sextortion refers to the broad category of sexual exploitation in which abuse of power is the means of coercion, as well as to the category of sexual exploitation in which threatened release of sexual images or information is the means of coercion.
Not only are bad actors harvesting emails and passwords for credential stuffing, they are also potentially blackmailing people in your team.
Though the problem goes even further.
Much of our online footprint is intertwined… and can be unwound very quickly.
Even if you only use your personal email to sign up to porn sites, it’s still easy to find out where you work. Who your partner is. Where you go on holiday.
Did you use the same personal email to sign up to Facebook or LinkedIn? Did you add both your personal and work addresses to these services? Thus making reconnaissance even easier.
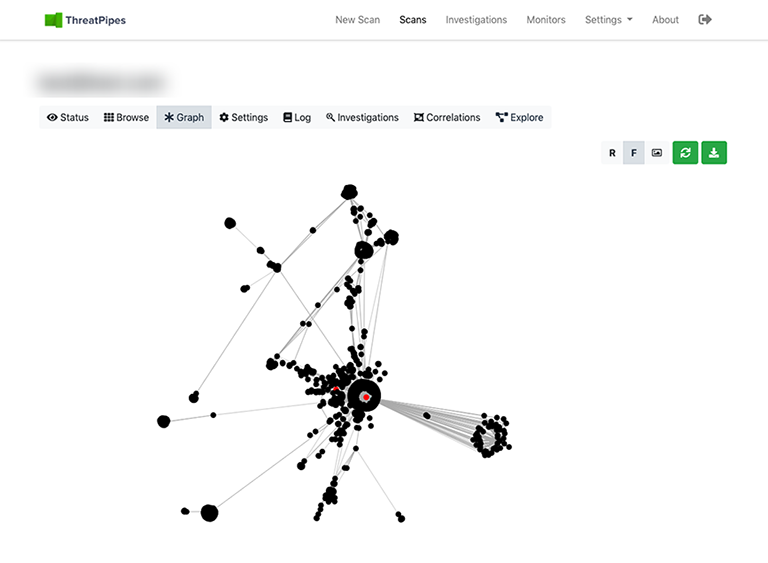
I was recently working with a customer to identify such risks.
High-value targets in their company were being targeted based on job description and previously leaked credentials from personal accounts.
The graph above shows a network graph of how their employee data was being shared around the internet and dark web (over 1000 data points!).
I’m sure you’ve heard the old adage; don’t mix business with pleasure.
I propose a new one;
If you really, really, must sign up to a porn site, use a disposable email.
Needs some work I think…
ThreatPipes Modules relevant to this post
- HaveIBeenPwned: Check Have I Been Pwned? for hacked e-mail addresses identified.
- Pastebin: Search Pastebin to identify related content.
- Psbdmp: Check psbdmp.cc (PasteBin Dump) for potentially hacked e-mails and domains.
- Social Networks: Identify presence on social media networks such as LinkedIn, Twitter and others.

