site: threatpipes.com allintext:"google dorks"
What is the juiciest piece of information you’ve ever found during reconnaissance?
A question recently posed to me during a conference.
Let me say it originated in the office of a very prominent person.
Credentials, documents, private keys, configuration files, database dumps. The internet is littered with these nuggets of intelligence.
Sometimes broad searches can turn up results. Log files are often interesting. site:*/logs/default.htm.
But they’re noisy.
Narrowing it down to allintext:username filetype:log produces nicer results.
Sometimes log file dorks will pull up database dumps. Good.
filetype:env APP_ENV. Environmental variables. Better.
You can search specific variables too. intext:DB_PASSWORD ext:env.
A users private key. ext:ppk ssh key -github.com -gitlab. Best.
Don’t forget to look at their site directly, perhaps they’re users are directly vulnerable.
No SSL? site:threatpipes.com -inurl:https
Though my absolute favourite dorks are filetype:pdf and filetype:docx.
If I’m trying to dig up some information on a target, my searches will start along the lines of filetype:pdf "Person Email" or filetype:pdf "Person Phone".
Invoices, internal documents, meeting notes… there’s a lot to be found that should not be out there.
Excel documents can be even more fruitful. The world is managed by spreadsheets. filetype:xls.
And so are many peoples account passwords by the looks of it. s3 site:amazonaws.com filetype:xls login.
It’s amazing how many of my clients in financial services expose market sensitive in Powerpoint presentations too. filetype:ppt.
And of course, don’t forget the cached versions.
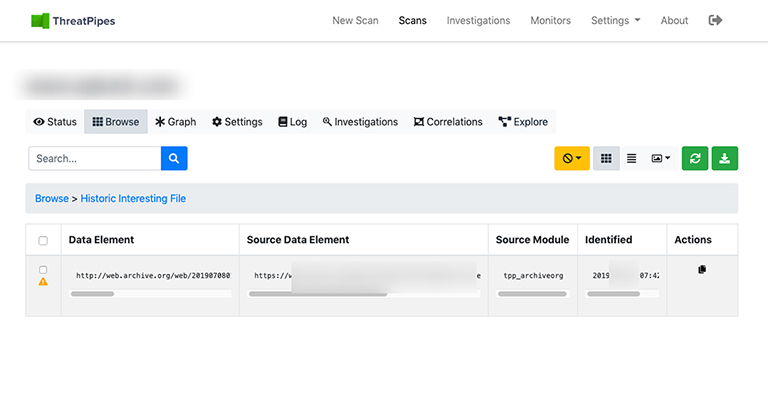
That accidental commit, or document made public might have been archived by Google, et al. I’m looking at you archive.org.
filetype:pdf cache:threatpipes.com
ThreatPipes Modules relevant to this post
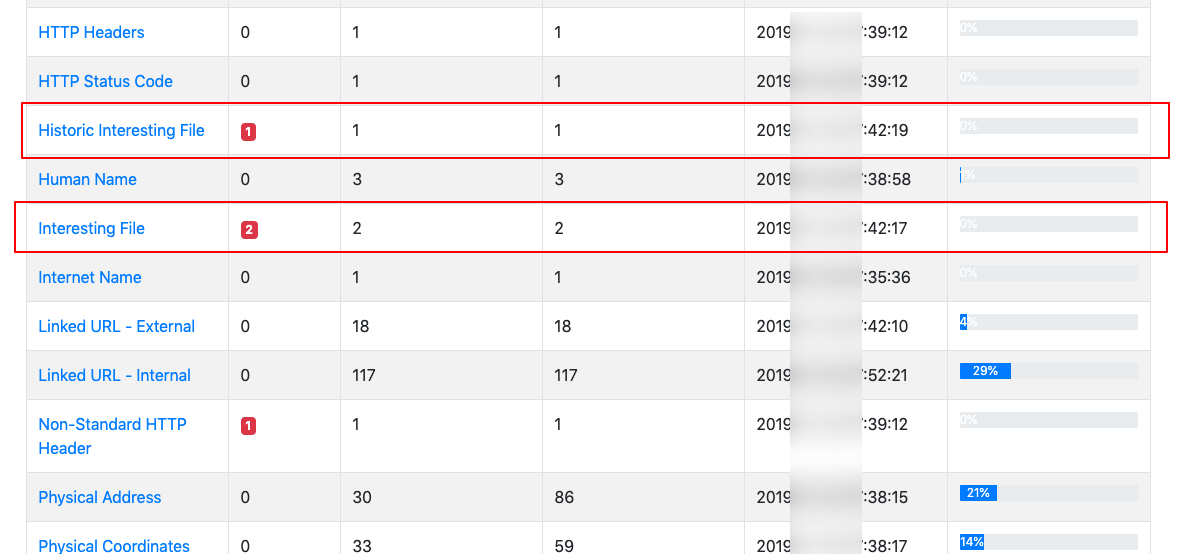
- Interesting files: Identifies potential files of interest, e.g. office documents, zip files.
- Junk files: Looks for old/temporary and other similar files.
- Pastebin: Search Pastebin to identify related content.
- Archive.org: Identifies historic versions of interesting files/pages from the Wayback Machine.
- S3 bucket finder: Search for potential Amazon S3 buckets associated with the target and attempt to list their contents.

