It was the night before Christmas…
OK. That’s enough of that.
Has anyone noticed an increase in phishing emails from logistics companies recently?
As the last minute Christmas rush takes hold, many of us have probably attempted to get those last minute online orders in on-time.
Sadly I didn’t. I’ll be heading out at lunchtime to buy those last remaining gifts.
Finding out a package wasn’t delivered is frustrating at the best of times.
The stress of Christmas can amplify it.

The urgency can cause even the best of us to lower our guard and open the attachment or follow the link of a time-sensitive email.
And as the familiar story goes; the mouse button clicks, the payload is executed.
Security awareness training helps educate staff of these risks, and is probably the most important part of a security strategy.
But phishing campaigns tap into a sense of urgency, from unpaid invoices to requests from “the CEO”.
Emotet’s annual season’s greetings are here: the gang has launched its campaign for holidays with email subjects and malicious attachment file names like “Party menu”, “Christmas party”, “Holiday schedule 2019-2020”. pic.twitter.com/tCgoENbYw5
— Microsoft Security Intelligence (@MsftSecIntel) December 14, 2019
The team at Microsoft highlight a good example in Emotet’s annual season’s greetings with email subjects and malicious attachment file names like “Party menu”, “Christmas party”, “Holiday schedule 2019-2020”.
This sense of urgency can quickly cause even the most well produced online training videos (anyone found any yet?) to be forgotten.
But lets take a look at how obvious these phishing emails actually are to the trained eye.
Using a real DHL phishing email I was gifted this holiday season, opening the extension (in a sandbox) I find the malware attached is reporting back to the domain:
tiqfgpaxvmhsxtk[.]com
I don’t want to let the target know I’m performing reconnaissance, so I’ll use passive reputation system modules in ThreatPipes to take a covert look.
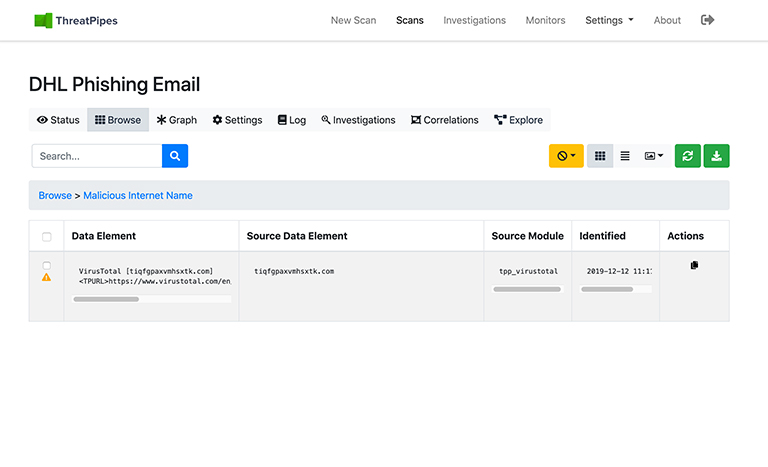
Interesting…
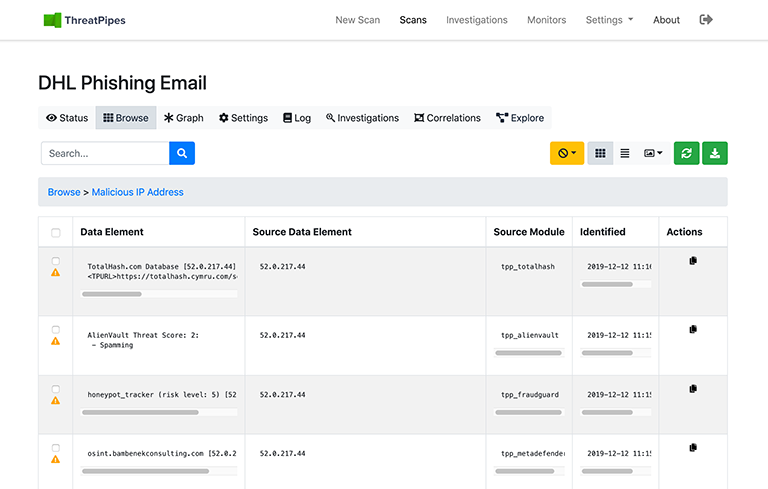
ThreatPipes also uncovers that the domain resolves to an IP.
52[.]0[.]217[.]44
That IP has been reported as malicious to 5 of the modules that scanned it (TotalHash, AlienVault OTX, Fraudguard, MetaDefender, VirusTotal)
Time to block that IP.
But what else has ThreatPipes found?
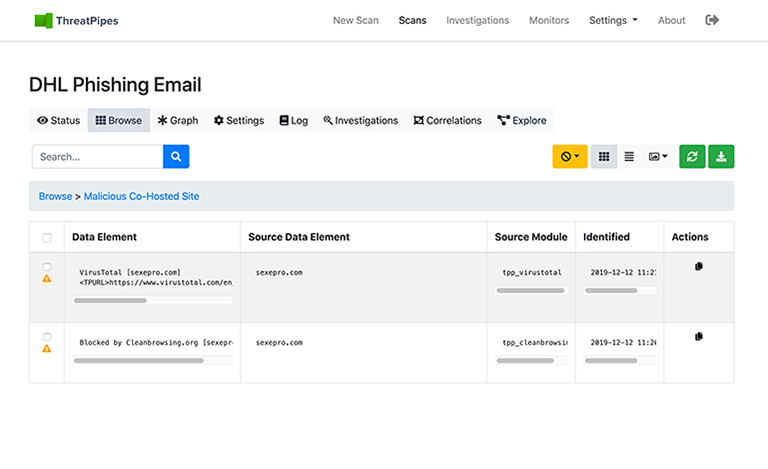
There are other sites hosted on the same IP… All of which are also hosting malicious content.
Blocked.
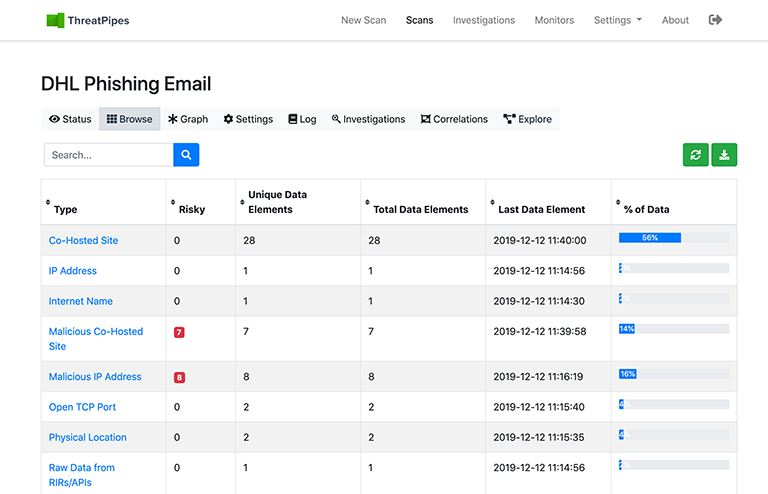
Oh, and some affiliate IPs reported as malicious probably belonging to the same group or lone bad actor.
Time to block those too.
ThreatPipes also found a couple of Dark Web mentions, an SSL Certificate mismatch on the domain, along with some strange headers, and Flash content thrown in for good measure.
By collecting everything we know about this threat, versus simply blocking the original malicious domain, I’m now better prepared for secondary attacks as those targeting me use other assets in their arsenal.
And that’s how Christmas was saved.
Happy holidays!
ThreatPipes Modules relevant to this post
- AlienVault OTX: Obtain information from AlienVault Open Threat Exchange (OTX)
- Fraudguard: Obtain threat information from Fraudguard.io
- TotalHash: Check if a host/domain or IP is malicious according to TotalHash.com.
- MetaDefender: Search MetaDefender API for IP address and domain IP reputation.
- VirusTotal: Obtain information from VirusTotal about identified IP addresses.

