Most corporate emails are easy to decipher. They’re boring.
I’d estimate; firstname.lastname@company, firstinitiallastname@company, or name@company cover 99% of organisation email formats.
dgreenwood@threatpipes, david.greenwood@threatpipes, and david@threatpipes. One (or more) of these will get your email in my inbox.
It’s the same story with file directory names.
Unlike phone numbers, trial and error will quickly get you in contact with someone via email.
Even better, services like Hunter will pull email addresses and email formats with no guesswork required.
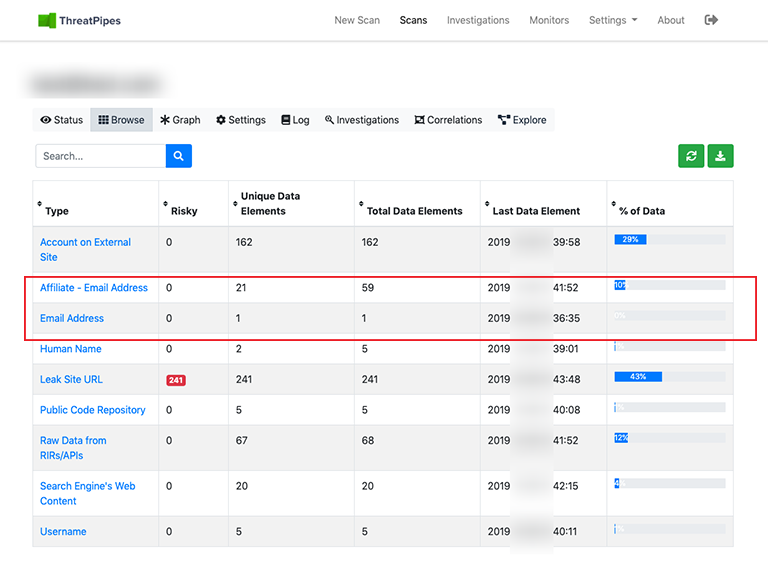
Other services will also uncover other known artefacts associated with the email address, for example Full Contact might show linked social media accounts. Or HaveIBeenPwned turning up a breached account.
This make targeting employees easy.
Dear David, please renew your LinkedIn Premium account today. Click here to renew.
Other organisations employ more obscure email address formats.
My favourite are some of the addresses the UK military assign to shared mailboxes. Examples include; aspt-gra-smi@, 3gbn-xo-csc@, and dcyp-mod-esf-mailbox@.
I’m not exactly sure why they do this. Neither are the holders of such email addresses.
I remember receiving an email where the username was over 50 characters long!
When I met this person months later they handed me their business card. The printed email address took up two lines.
Hunter will uncover these types of address too, and thankfully where they were sourced from, allowing you to make an educated guess what usernames like dcyp-mod-esf-mailbox@ are used for or who they are used by.
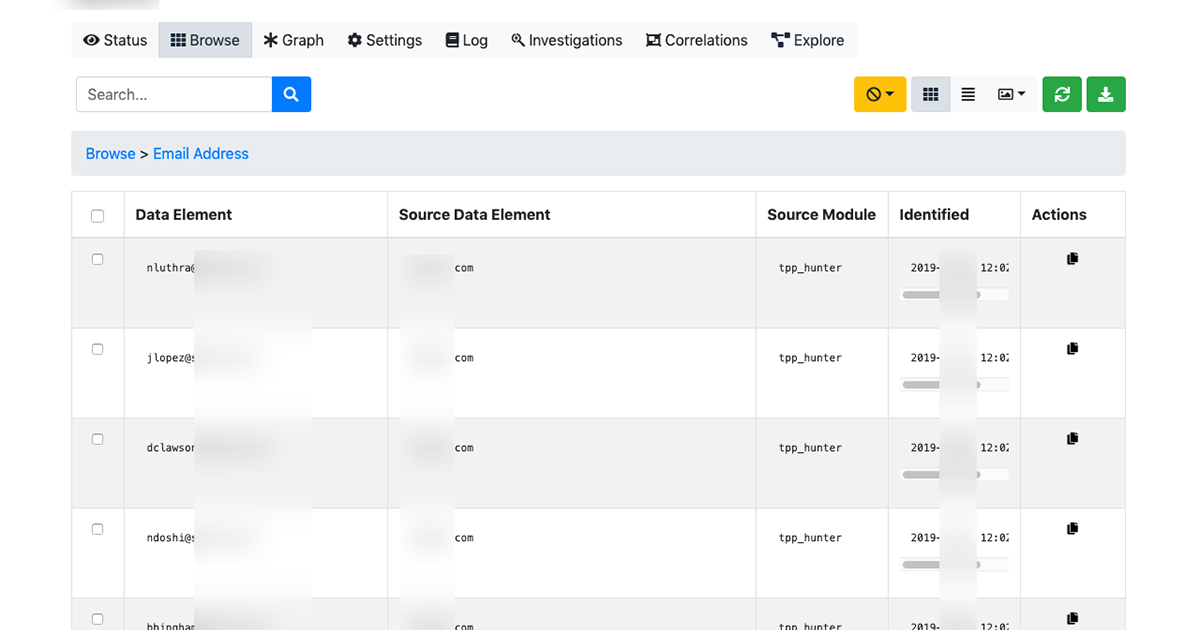
Though my absolute favourite addresses are the shared inboxes of security teams.
siem@company, soc-alerts@company, ir@company, etc.
Security teams often have the highest privileges. They are a high-value targets.
Combine that with the fact many companies will promote the vendors they’re working with, or just expose them to the internet (thank you Shodan, Censys et al.), it makes the perfect recipe for a well targeted attack.
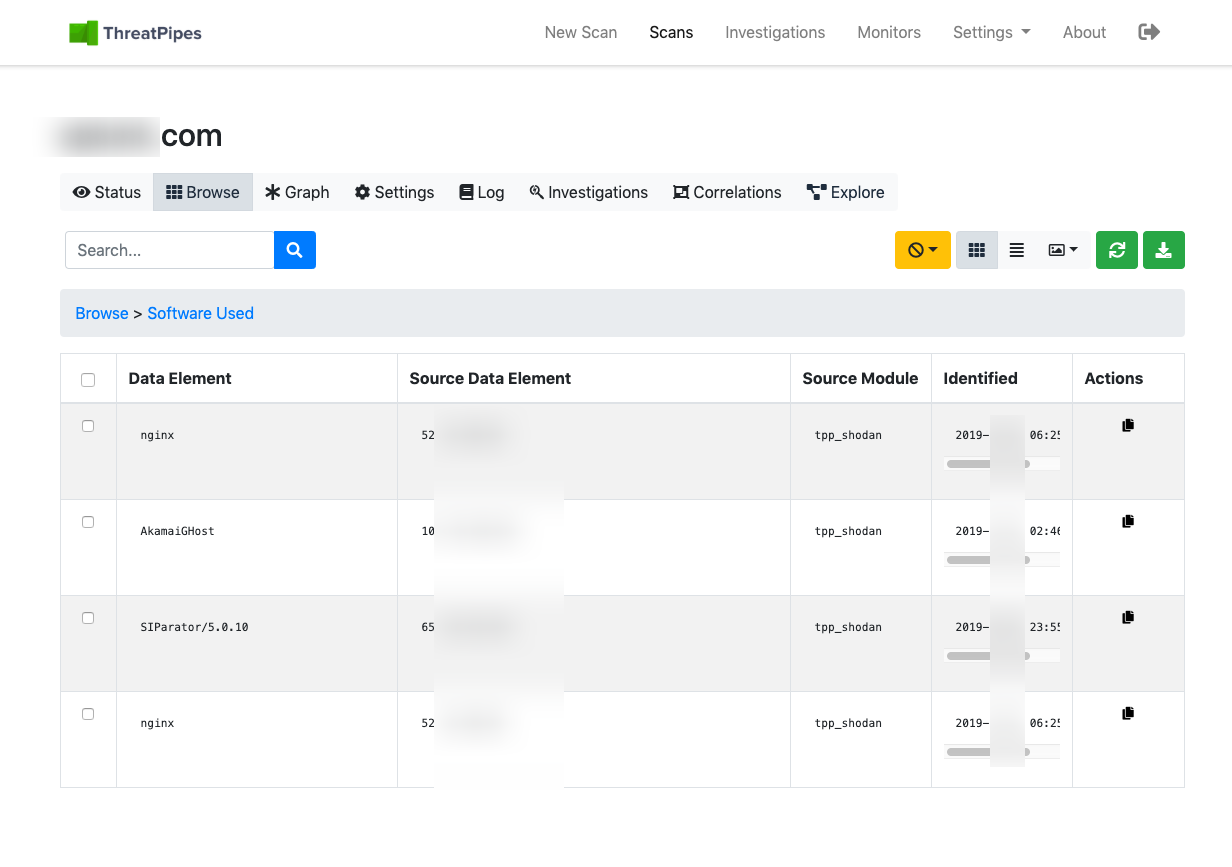
Using Splunk for your SIEM?
I’ll craft convincing looking email mimicking a security incident… linking to a payload.
PagerDuty?
Quick, quick, quick! Check this alert…
If I’m lucky, six or seven analyst in the team might click that email. Though I’ll take just one.
ThreatPipes Modules relevant to this post
- Hunter: Check for e-mail addresses and names on hunter.io.
- Censys: Obtain information from Censys.io
- EmailRep: Search EmailRep.io for email address reputation.
- HaveIBeenPwned: Check Have I Been Pwned? for hacked e-mail addresses identified.

